Customised Cyber Security for Complete Protection
Cyber Security Services London – What’s Included
Looking for robust Cyber Security Services to protect your business and ensure data integrity?
At Unified IT, our experts deliver comprehensive security solutions tailored to your needs, safeguarding your operations from cyber threats.
Crafted For Your Success
Why Our Cyber Security Services Work for London Businesses
Concerned About Cyber Threats — Whether You’re in London or Operating Globally? We help protect your business with proactive monitoring and tailored security solutions that keep your data safe and your operations running smoothly.
No matter where you work, you’ll stay ahead of evolving threats with reliable protection built for your unique needs.
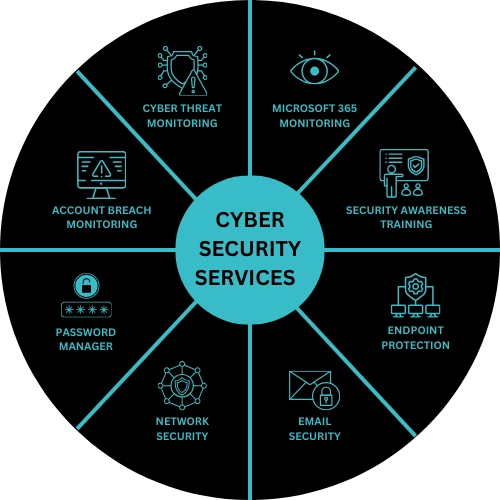
Don’t let cyber threats put your business at risk. With Unified IT by your side, you’ll get reliable, proactive cybersecurity solutions that help you navigate the digital world with confidence. Ready to secure your business? Get in touch with us today to see how we can protect you from cyber threats.
-FAQs-
Cyber Security Services FAQs
Looking for answers about cyber security? Our FAQs section covers everything you need to know—from why cyber security is essential for businesses to understanding different types of threats and ways to reduce risks. You’ll find valuable insights to help protect your organisation’s digital assets, whether you’re aiming to strengthen your security, stay compliant, or tackle the challenges of cyber threats. Our FAQs provide practical guidance and solutions designed with your needs in mind.

Let’s Talk About Your IT Needs
No spam. No endless calls. Just a quick, easy way to get started.
Book a free consultation with Tariq to talk through your IT challenges, goals, and hidden risks. Whether you’re in London or beyond, you’ll get clear, expert advice on the best next steps for your business.
Pick a time that suits you on the calendar to the right. We’ll chat about your needs and create a tailored plan with personalised pricing—no obligation at all.
Just choose a time and let’s get the ball rolling!
